As a part of an educational lab environment our teacher set up “Ninja Hacker Academy” (NHA).
The only information we received was a list of hosts
| IP | Hostnames |
|---|---|
| 10.9.10.30 | dc-vil dc-vil.ninja ninja |
| 10.9.10.31 | dc-ac dc-ac.academy academy |
| 10.9.10.32 | web web.academy.ninja |
| 10.9.10.33 | sql sql.academy.ninja |
There is a Linux host with Kali on the same network, that we can use as our hacking platform.
We access the 10.9.10.0/24 net through a “tailscale”-connection that is not routing back to our own host, which means that reverse shells will be a bit hard to accomplish, although we can always reverse back to the Kali-machine on the 10.9.10.x – network.
Let’s start of by enumerating the network
Enumerations
Lets make some recon and enumerations and see what we find.
Nmap
Running a simple nmap scan of the subnet provides this information:
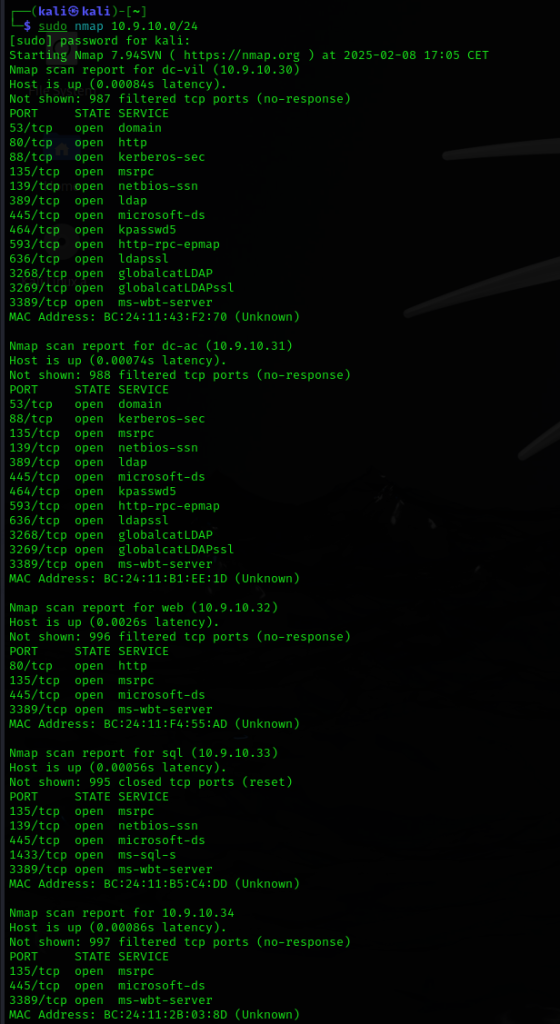
(there were some other hosts on that subnet as well, but as they are a part of the infrastructure for the NHA, I choose to omit them for clarity)
Conclusions:
10.9.10.30 – dc-vil
| TCP port | Description | Comment |
|---|---|---|
| 53 | domain | DNS server |
| 80 | http | Web server http |
| 88 | kerberos-sec | Kerberos authentication service |
| 135 | msrpc | Microsoft RPC |
| 139 | netbios-ssn | Filesharing SMB |
| 389 | ldap | LDAP |
| 445 | microsoft-ds | Filesharing SMB |
| 464 | kpasswd5 | Kerberos password change service |
| 593 | http-rpc-epmap | RPC over HTTP, used in DCOM services |
| 636 | ldapssl | LDAPSSL |
| 3268 | globalcatLDAP | Global Catalog LDAP |
| 3269 | globalcatLDAPssl | Global Catalog LDAP SSL |
| 3389 | ms-wbt-server | Remote Desktop Protocol (RDP) |
There are several indications that this is Windows AD DC (port 53, 88, 389, 3268 and 3269)
Also we can learn that RPC, file sharing, RPC over HTTP and RDP is enabled as services that we might be able to communicate with.
The http service is also active implying some sort of unencrypted web service running.
10.9.10.31 – dc-ac
| TCP port | Description | Comment |
|---|---|---|
| 53 | domain | DNS server |
| 88 | kerberos-sec | Kerberos authentication service |
| 135 | msrpc | Microsoft RPC |
| 139 | netbios-ssn | Filesharing SMB |
| 389 | ldap | LDAP |
| 445 | microsoft-ds | Filesharing SMB |
| 464 | kpasswd5 | Kerberos password change service |
| 593 | http-rpc-epmap | RPC over HTTP, used in DCOM services |
| 636 | ldapssl | LDAPSSL |
| 3268 | globalcatLDAP | Global Catalog LDAP |
| 3269 | globalcatLDAPssl | Global Catalog LDAP SSL |
| 3389 | ms-wbt-server | Remote Desktop Protocol (RDP) |
Similar findings for this server
The apparent difference is that there are no http service running on this one
10.9.10.32 – web
| TCP port | Description | Comment |
|---|---|---|
| 80 | http | Web server http |
| 135 | msrpc | Microsoft RPC |
| 445 | microsoft-ds | Filesharing SMB |
| 3389 | ms-wbt-server | Remote Desktop Protocol (RDP) |
This looks like a windows based computer with a webserver on it.
10.9.10.33 – sql
| TCP port | Description | Comment |
|---|---|---|
| 135 | msrpc | Microsoft RPC |
| 139 | netbios-ssn | Filesharing SMB |
| 445 | microsoft-ds | Filesharing SMB |
| 1433 | ms-sql-s | Microsoft SQL |
| 3389 | ms-wbt-server | Remote Desktop Protocol (RDP) |
And this looks like a MS SQL server
Interestingly enough there are one more host on the network that the teacher didn’t give us in the list.
Let’s see if it is of interest
10.9.10.34 – ?
| TCP port | Description | Comment |
|---|---|---|
| 135 | msrpc | Microsoft RPC |
| 445 | microsoft-ds | Filesharing SMB |
| 3389 | ms-wbt-server | Remote Desktop Protocol (RDP) |
Smells like Windows to me.
Lets see if we can find out more about each of these hosts.
Netexec
nxc smb 10.9.10.30-34
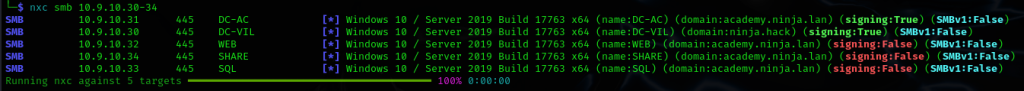
We find out that .34 is called share. My guess is that it’s a part of the lab,
We also get some extra interesting clues.
- DC-AC and DC-VIL looks like Domain Controllers. Partly because of their name, partly because of what services they are running
- SMBv1 is not enabled – Eternal blue and similar attacks will not work
- SMB Signing is disabled for .32-.34 which could be exploited in relay attacks.
nmap service version scan
sudo nmap -sV -p 80,135,445,3389 10.9.10.30-34
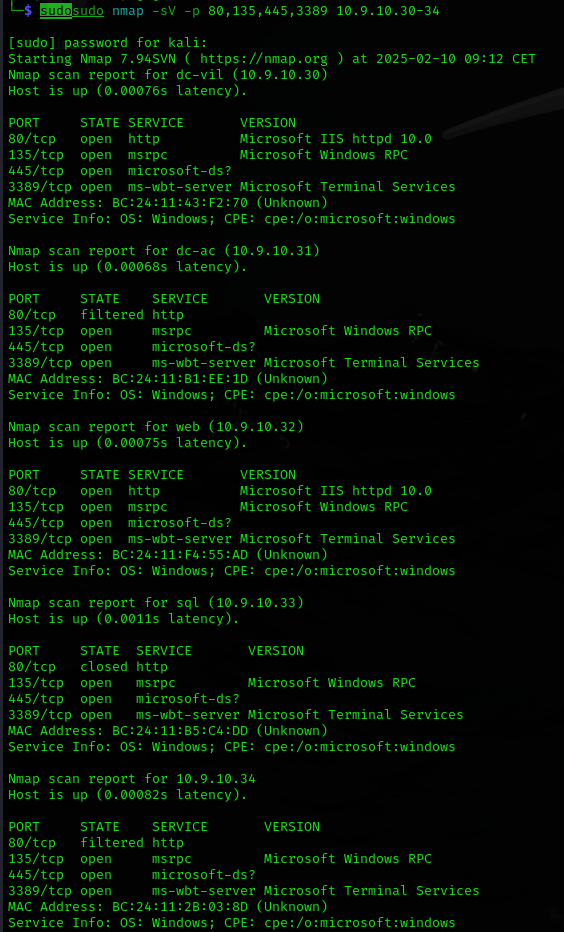
The only interesting information here is that it is running Microsoft IIS httpd 10.0.
This is default for Windows Server 2016/2019 and if it’s not properly patched there are some known vulnerabilities that we will look for later.
We didn’t get the SMB versions and available shares so lets start looking for that
smbclient share scan
smbclient -L \10.9.10.x –no-pass
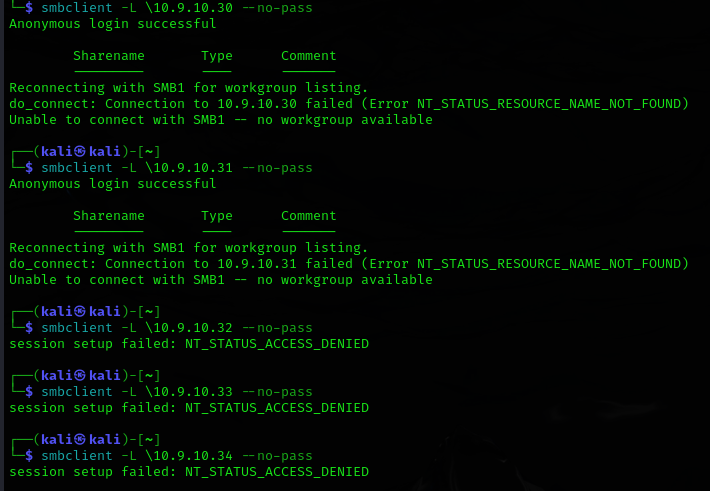
- The DC’s allows anonymous access but the shares are restricted
- No anonymous access for web, sql and share
nmap smb-protocols scan
sudo nmap –script smb-protocols -p 445 10.9.10.30-34
The results are very lengthy, so I will not post a full screenshot. But this is repeated for all hosts:
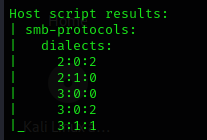
SMBv2 (2.0.2 and 2.1.0) and SMBv3 (3.0.0, 3.0.2 and 3.1.1) are supported.
This confirms that SMBv1 is not active.
But as we previously discovered, signing is not enabled on .32-.34 which we will try to exploit later on.
smbmap
smbmap –host-file nha_hostfile.txt
(nha_hostfile.txt is a list of the 5 IP’s)
Guest/anonymous access is not allowed or has no visible shares. Looks like we would need to find some credentials to get in to any shares.
rpcclient NULL sessions
rpcclient -U “” -N 10.9.10.30
NULL sessions not allowed
This means we need to find valid credentials to be able to enumerate with SMB or RPC
kerbrute user enumeration
./kerbrute_linux_amd64 userenum -d ninja.hack –dc 10.9.10.30 ~/Downloads/xato-net-10-million-usernames.txt
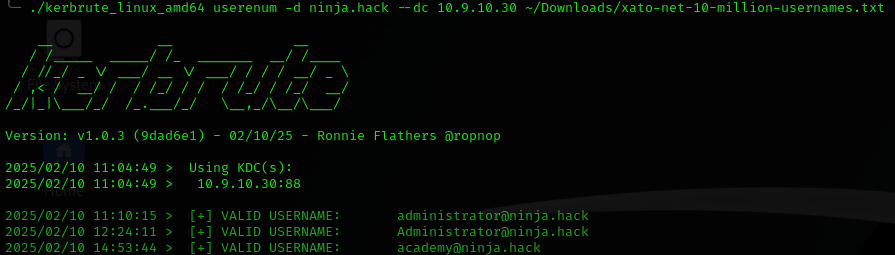
After about 12 hours running 2 users were found in the ninja.hack-domain:
administrator@ninja.hack and academy@ninja.hack
./kerbrute_linux_amd64 userenum -d academy.ninja.lan –dc 10.9.10.31 ~/Downloads/xato-net-10-million-usernames.txt
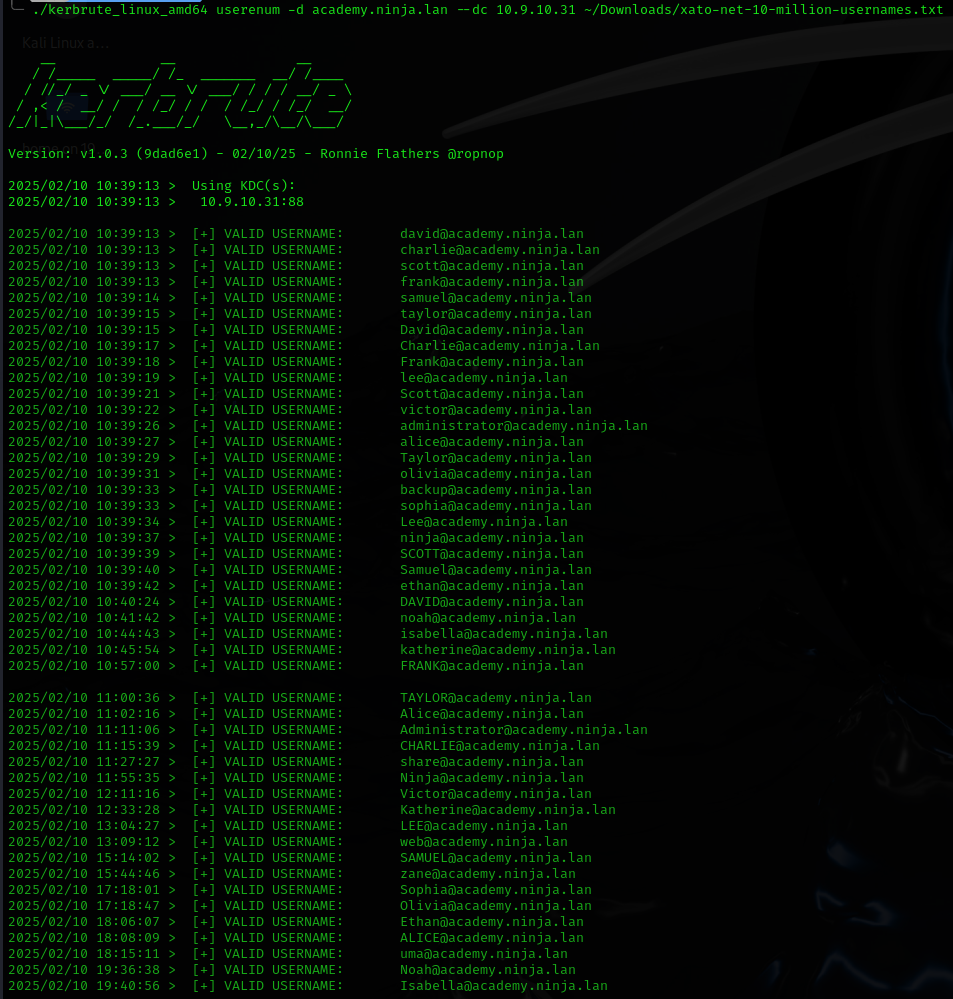
administrator@academy.ninja.lan
alice@academy.ninja.lan
backup@academy.ninja.lan
charlie@academy.ninja.lan
david@academy.ninja.lan
ethan@academy.ninja.lan
frank@academy.ninja.lan
isabella@academy.ninja.lan
katherine@academy.ninja.lan
lee@academy.ninja.lan
ninja@academy.ninja.lan
noah@academy.ninja.lan
olivia@academy.ninja.lan
samuel@academy.ninja.lan
scott@academy.ninja.lan
share@academy.ninja.lan
sophia@academy.ninja.lan
taylor@academy.ninja.lan
uma@academy.ninja.lan
victor@academy.ninja.lan
web@academy.ninja.lan
zane@academy.ninja.lan
Let’s call it a day and tomorrow we look at if we can find any exploits from the gathered information!

Leave a Reply